BruCON Training: Module 1, An Introduction to ...
An Introduction to VoIP technology, security threats and solutions, module 1. This module allow us to set the stage for the rest of the training. We will introduce the players - Asterisk, Cisco unified communications and other products. We will introduce the protocols briefly - SIP, SCCP (Skinny), IAX2, H.323 and MGCP. We will also look at how VLANs and other solutions are used to provide security (and where they fail).
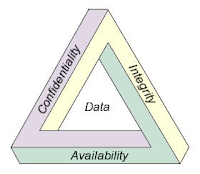
We will then focus on security in terms of confidentiality, integrity and availability without going into too much detail (just to wet your appetite ;-)).
Confidentiality
When it comes to VoIP, confidentiality ensures that the communications -
phone calls and any signaling data - cannot be spied upon.
Confidentiality is a major weakness in the case of many VoIP systems.
One obvious security issue is when internal attackers spy on phone calls
by sniffing the RTP stream. However this is not the only attack vector.
We will give examples of tricks that can be pulled off by external
attackers that allow them to compromise confidentiality remotely,
without (layer 2) access to the network.
Integrity
Caller ID spoofing, toll fraud and modification of signal or media
affects the integrity of the VoIP system. In this section we will look
at these and various other security flaws that do not necessarily allow
attackers to gain illegal access to confidential information. These
security flaws however, may allow attackers to cause organizations to
loose large sums of money.
Availability
This tends to be the security flaw that really affects organizations
directly. When the phone system is down, many organizations suffer. This
is especially true for call centers, which base their revenues on phone
calls. With VoIP, attackers can abuse flaws at various levels to cause
denial of service. In this section we will introduce some attacks that
are specific to VoIP and others that affect systems in general.