11 million Euro loss in VoIP fraud .. and my VoIP logs
And the attackers made over 1 million in profits.
This just emerged from a raid (and hearing apparently) in Romania and
other countries. The two main persons being fingered are Catalin Zlate
and Cristian Ciuvat. It seems that they were scanning for PBX servers
with phone extensions that have weak passwords. Then they abused these
accounts to make phone calls for “free”, except that free has the price
of 11 million EUR for the victims!
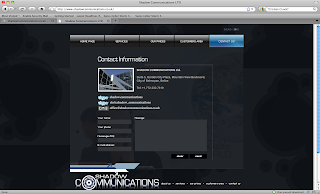
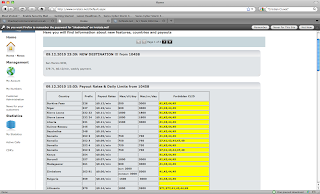
Apparently, originally they used these accounts for their own personal phone calls. However they got greedy and between October 2009 to February 2010, they made 23500 calls / 315000 minutes to premium numbers. Then (from what I understood), they got even more greedy and used Shadow Communication Company Ltd. This site is still available right now - whois shows the name of Cristian Ciuvat (thanks for someone on pointing this out). This site contains lists of prices for premium numbers, linking to another site Ivrstats.net. Using this they recruited other people to make 1,541,187 fraudulent calls or 11,094,167 minutes of talk time.
So right now there are 42 people in court with raids happening in London, Neamt, Brasov, Cluj and Maramures. This is all according to various sites in Romanian, translated automatically using Google translate.
One of the original articles on this can be found here.
Here’s a screenshots from their site (in case it goes down):
Some thoughts
On our honeypots we have seen Zoiper messages from Romania and this could possibly be very related. I decided to check out my logs and sure enough found the sort of behavior described in the articles describing the illegal activities. The following IP addresses had Zoiper in their user-agent header when connecting to my simple VoIP honeypot:
- 89.42.156.102 - Romania
- 74.115.0.25 - US (San Jose)
- 68.194.64.146 - US - Brooklyn
- 74.115.0.24 - US (San Jose)
- 89.42.194.224 - Romania
- 79.117.27.97 - Romania
- 89.42.187.151 - Romania
- 64.9.175.89 - US (Austin)
- 95.76.211.188 - Romania
- 109.99.35.113 - Romania
- 85.186.123.121 - Romania
- 95.22.116.11 - Spain
Here’s an example SIP message that was sent from the 1st IP:
INVITE sip:0040767091012@X.X.X.X;transport=UDP SIP/2.0
Via: SIP/2.0/UDP 89.42.156.102:5060;branch=z9hG4bK-d8754z-07cf25937cf90e2a-1---d8754z-
Max-Forwards: 70
Contact: <sip:1234@89.42.156.102:5060;transport=udp>
To: <sip:0040767091012@x.x.x.x;transport=udp>
From: "Unknown"<sip:1234@x.x.x.x;transport=udp>;tag=ce2e1a65
Call-ID: NmNhZTE5MGMwM2IyMDg3OTM5YWY1YTQ5OWYzZWYzNDE.
CSeq: 1 INVITE
Allow: INVITE, ACK, CANCEL, BYE, NOTIFY, REFER, MESSAGE, OPTIONS, INFO, SUBSCRIBE
Content-Type: application/sdp
User-Agent: Zoiper rev.6751
Content-Length: 329
v=0
o=Zoiper_user 0 0 IN IP4 89.42.156.102
s=Zoiper_session
c=IN IP4 89.42.156.102
t=0 0
m=audio 8000 RTP/AVP 3 0 8 110 98 101
a=rtpmap:3 GSM/8000
a=rtpmap:0 PCMU/8000
a=rtpmap:8 PCMA/8000
a=rtpmap:110 speex/8000
a=rtpmap:98 iLBC/8000
a=fmtp:98 mode=30
a=rtpmap:101 telephone-event/8000
a=fmtp:101 0-15
a=sendrecv
The phone number that the Zoiper user tried calling was “0040767091012”. Romanian numbers start with +40, so one can assume that this is some phone that the attacker was using to see if the call is terminated or not. This number is not a premium number. I have looked at other logs and some were probably premium numbers.
Note regarding Catalin Slate: is this the same person who was in 2005 caught with credit card fraud (reference here)?
I would be interested in hearing more about this case as it sheds some light on what’s actually happening in the background.
Update:
Thanks goes to Stefan Tanase for pointing
out the original article in Romanian. The also added the following:
As far as I understand, they were using other premium numbers affiliate networks at first and then, when they realized the potential, they set up a company in the UK - Shadow Communications Inc. - through which they were able to sign a contract on their own with a premium rate number provider and offer their own affiliates service, basically taking their “business” to a whole new level.
Conclusion
All in all, it looks like these attackers were not so technically advanced after all, yet managed to hit the million euro mark. I wonder what more skilled and stealthy criminals are able to do!